
Source: Compound Governance X
Compound is one of the oldest DeFi protocols. Aside from phishing attacks on websites or X, it has never experienced hacking due to significant flaws. It is a pioneer in liquidity mining and currently holds deposits worth about $1.8 billion (as of August 6, 2024) across various networks. Despite the rise and fall of many DeFi protocols, one reason Compound has remained is its strict decentralization. Compound implemented this through Compound Governance, allowing any user to participate in Compound governance via COMP tokens, which can be obtained by depositing assets within the Compound protocol or purchasing them from other exchanges.
However, the same decentralized governance that Compound took pride in became the cause of a significant internal collapse.
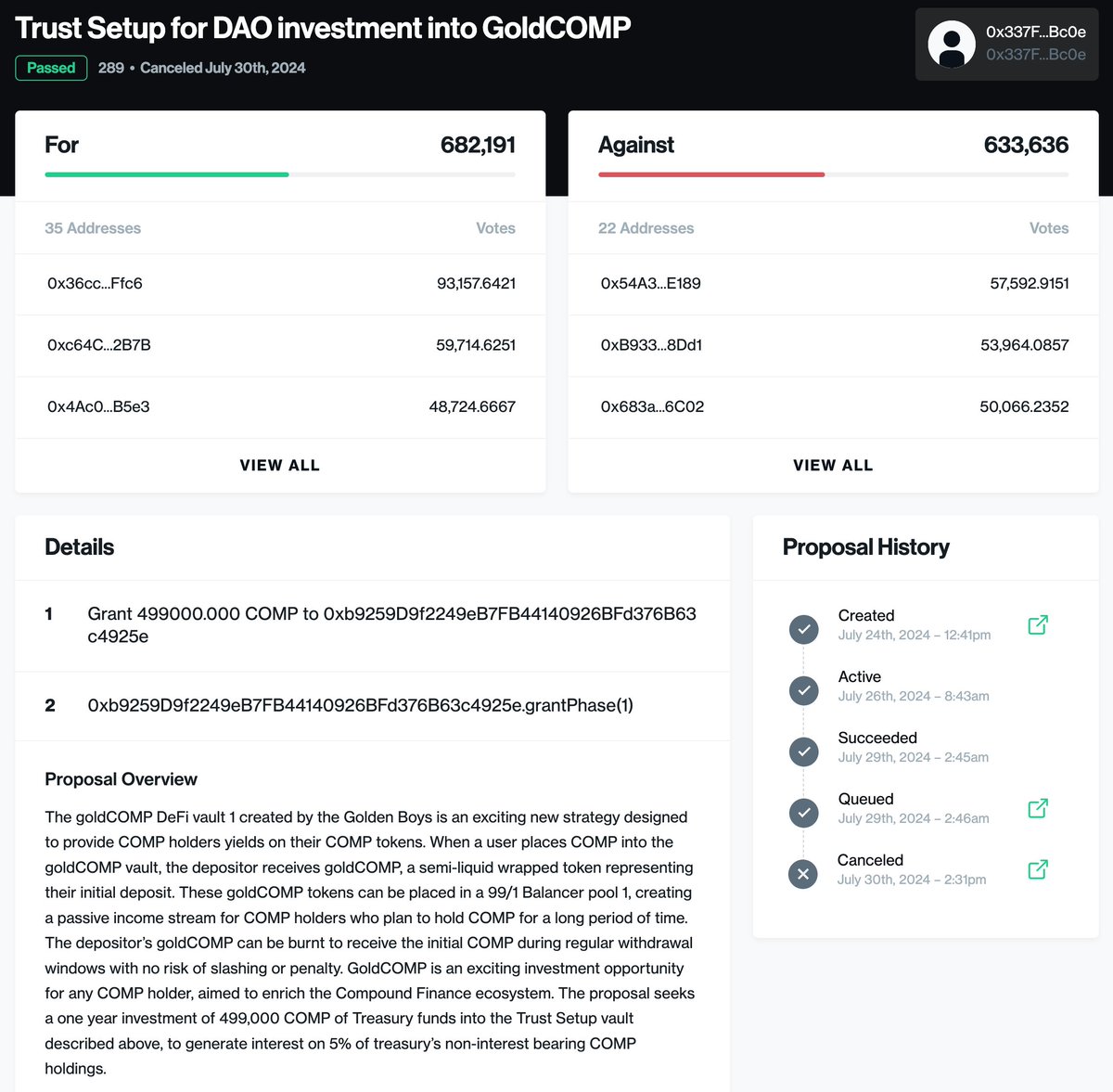
Source: Compound Governance Proposal #289
This incident, which caused a stir from July 29, 2024, started with the passing of Governance Proposal 289, which allocated a whopping 499,000 COMP tokens (worth approximately $24 million and accounting for 5% of the total COMP token supply) to a liquidity pool managed by a group known as the "Golden Boys." This group, led by a whale investor using the ID "Humpy," secured enough COMP tokens from other exchanges to force the passage of Proposal 289 despite opposition from governance participants and security experts within the governance.
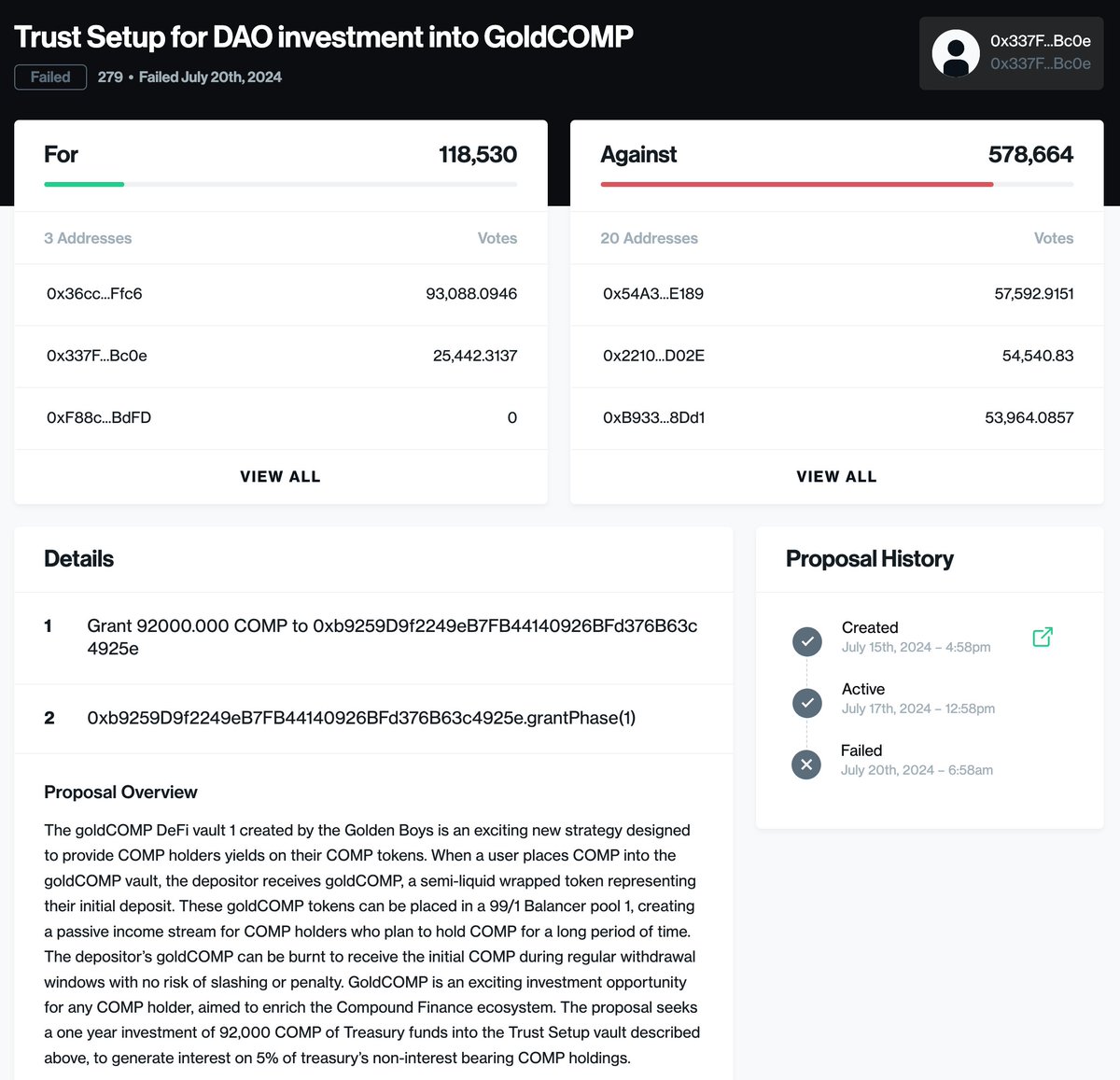
Source: Compound Governance Proposal #279
More shockingly, Proposal 289 was not the first attack. On July 20, 2024, the same proposer submitted Governance Proposal 279, which similarly attempted to allocate 92,000 COMP tokens using the same method but with a different number of tokens. Governance security expert Michael Lewellen discovered and warned about this proposal, preventing the attack. However, realizing the lack of interest within the Compound DAO members, the Golden Boys group increased the attack amount more than fivefold and re-attacked.
Fortunately, although Proposal 289 passed, it was canceled without execution, preventing the unprecedented situation where 499,000 COMP tokens would fall into the hands of a malicious proposer. However, other platforms with similar DAO structures are now vigilant and concerned.
The reason these series of events feel particularly fatal is that the attack occurred within the procedural legitimacy of the DAO system, which was considered fundamental to Web3 decentralization. Essentially, the proposal followed all the steps presented by Compound governance, except for the malicious intent to misappropriate COMP tokens for the proposer's investment.
The problem was the lack of broad participation from the Compound community. Only 57 addresses participated in the vote, a disappointingly low turnout given the size and asset scale of Compound governance. The Compound governance forum, which should have been actively self-regulating, remained silent at the critical moment.
Notably, Humpy, who executed this governance attack, is infamous for his track record. He has caused disturbances by attacking the governance of other DeFi protocols like Balancer and SushiSwap. Compound governance could have taken preventive measures from past examples but neglected them, leading to this dangerous moment.
So, what measures can be taken to prevent such attacks on DAO systems? This issue can be more complex and challenging than addressing other security threats in the blockchain industry. While bugs in smart contract code or system vulnerabilities can be resolved immediately by the developers, DAO systems require the unanimous agreement of multiple participants.
To prevent cases like the Compound governance attack, two preventative measures can be adopted:
1. Indirect Democracy Introduction
There are two main types of democracy: direct democracy and representative democracy. As the descriptions state, direct democracy involves the participation of all members, while representative democracy involves participation by only a few
theory, direct democracy where everyone participates may seem fairer and allow everyone’s influence to be evenly exercised. However, as the number of members in an organization or group grows, having all of them participate in decision-making becomes practically impossible due to spatial and temporal constraints. Additionally, if members lack awareness of participating in decision-making, an “apathetocracy” can arise where there are decision-making vacuums.This is why most democratic nations adopt a representative democracy system where citizens elect legislators to parliament to exercise decision-making power on their behalf. However, this representative democracy has the downside that if the representatives do not properly represent the opinions of their sovereign constituents, a gap can arise between the representatives and those represented.Source:
As mentioned in the author's previous writing, it would be ideal if all participants actively engaged, but realistically, apathy can occur. By delegating voting rights to proactive delegators, the decision-making process can continue. Many governance systems currently select delegators to carry on voting. However, if these delegators fail to fulfill their roles, it can lead to the same decision-making indifference, and centralization issues may arise. Therefore, continuous monitoring and interest from all participants are essential.
2. Reducing the Voting Impact of a Single Voter
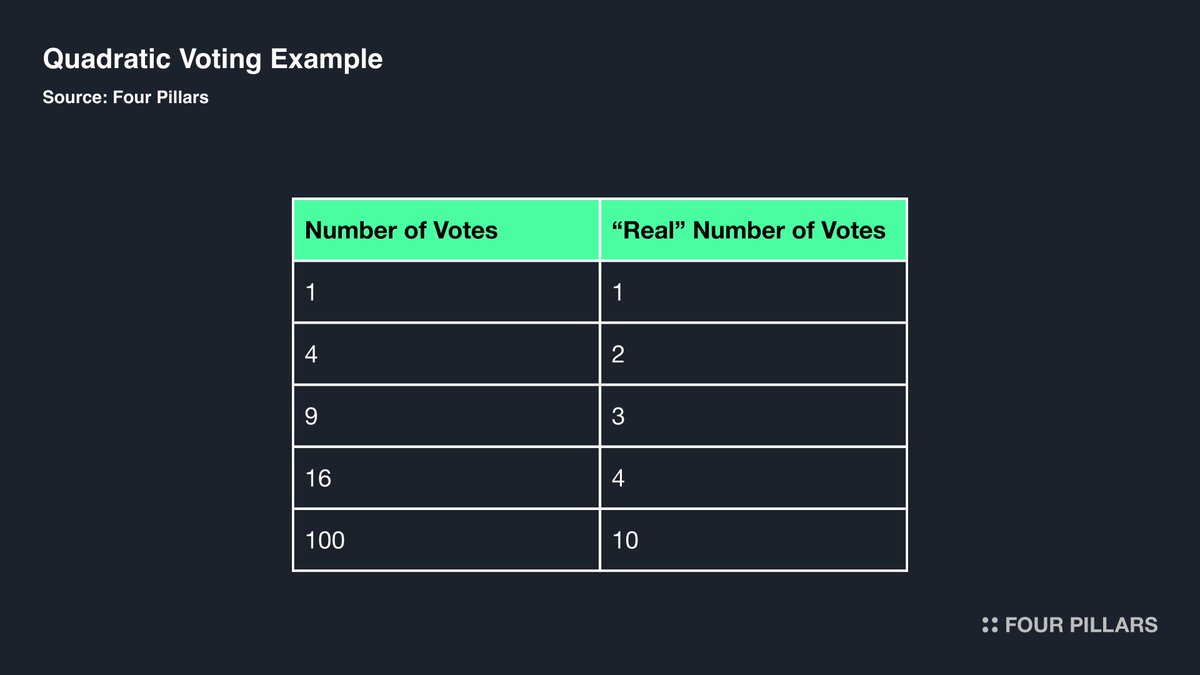
In this attack, Humpy met the quorum by purchasing sufficient COMP from external markets to achieve the required number of votes and counter the opposing votes. The nature of governance, where tokens equate to voting rights, cannot entirely eliminate the capitalist idea of buying votes. However, speed bumps can be installed to prevent resolving everything with money.
Quadratic Voting (QV) assigns vote weight based on the square root of the number of votes, reducing the voting weight of a single voter's bulk votes. While it cannot completely prevent attacks, it can serve as a barrier. Using QV or Probabilistic Quadratic Voting (PQV), which addresses QV's vulnerability to Sybil attacks, can help mitigate such attacks to some extent.
Once trust is lost in the Web3 ecosystem, it takes a considerable amount of effort and time to recover. This realization will be particularly painful for participants of a protocol that has lost trust. However, there is no one to blame but themselves. Despite the normal functioning of all procedures and processes, their absolute lack of "interest" led to the incident. While listing preventive measures, the most crucial factor is the participants' "interest."
This incident will serve as a wake-up call for other DeFi services. The key point is that decentralized governance can only be realized when participants remain vigilant and engaged. Otherwise, more governance attack cases that undermine the foundation of DAOs will occur.
Related Articles, News, Tweets etc. :
Dive into 'Narratives' that will be important in the next year