
※ This article series covers the DeFerence 2024 event, sponsored by Four Pillars, and will be published in three parts. This article is the first part of the series, and all attached presentation images were captured from the YouTube recording.
Part I - This Article
Part II - [Recap of DeFerence 2024] #2: Blockchain, Reaching the Masses
Part III - [Recap of DeFerence 2024] #3: Discussing the Present and Future of Blockchain Infrastructure
Academies play a crucial role in the development of industry by fostering continuous learning and knowledge sharing, which leads to the accumulation and advancement of new ideas and concepts. In the relatively nascent crypto industry, where knowledge is fragmented, academies promote balanced development through the exchange of knowledge.
One of the leading blockchain academies in Korea is Decipher. Founded at Seoul National University in 2018, Decipher has expanded its influence globally, contributing significantly to the blockchain ecosystem by producing numerous industry leaders. Decipher's successful operation has become a model, inspiring the creation of many similar academies domestically.
Under the mission of contributing to the healthy growth of the blockchain industry through technology development and value research, Decipher hosts an annual conference called ‘DeFerence’. This year's Deference, the seventh, focused on the theme 'Proof of Contribution', highlighting the initiatives and approaches of Decipher members in advancing the blockchain ecosystem.
This article series recaps the event in three parts, and each part consists of keynote speeches, panel discussions, and presentations by Decipher members. While it may not fully capture the vibrant networking atmosphere of the event, it aims to summarize the key presentations and personal impressions to provide a comprehensive understanding of the event. The full video of the event, conducted in Korean, can be viewed here.
The first theme of the conference was 'Contribute to the Blockchain Ecosystem'. This part featured keynote speeches on the social, economic, and industrial values expected from blockchain technology and case studies from Decipher members who have made direct contributions to the ecosystem.
Overview
Steve Kim from the global research firm Four Pillars pointed out that while there is extensive research on what technologies are innovative in the industry, not enough attention is given to the fundamental question of why blockchain is necessary. He shared insights on the core values and fundamentals of blockchain that many people resonate with or expect, and why continuous research in the industry is essential.
Comments
In the blockchain industry, we often observe a variety of new and diverse developments. For those directly involved in product creation, it is challenging to keep up with the fast-evolving industry trends and easy to become narrowly focused on one's field. As ecosystem builders, we frequently forget the fundamental values we aim to achieve with blockchain. This presentation allowed us to reflect on the core values we should focus on as industry participants to continue building the ecosystem.
Below is a summary of Steve Kim's presentation.
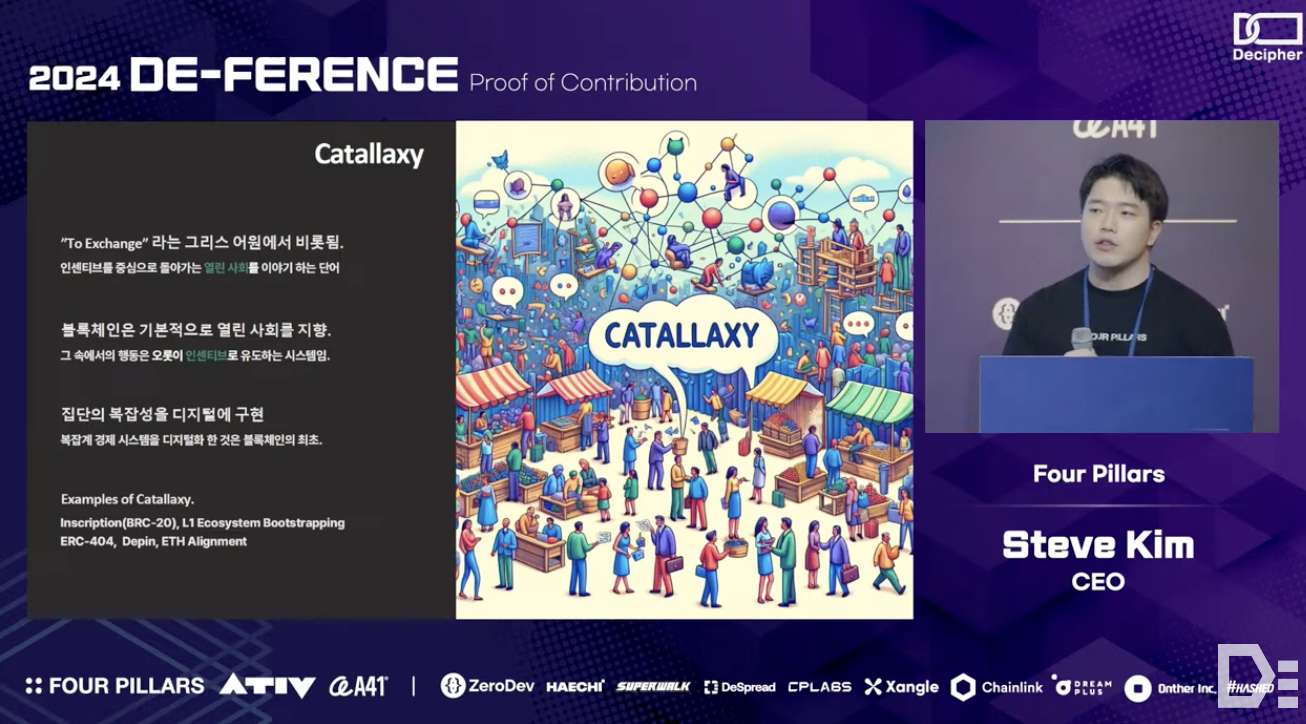
Friedrich Hayek, the 1974 Nobel Prize winner in Economics, proposed the term 'catallaxy' instead of 'economy' to describe markets. He argued that while 'economy' focuses on the collective allocation of resources, 'catallaxy' emphasizes voluntary exchanges driven by individual incentives. Therefore, he believed that 'catallaxy' better reflected the intrinsic value of markets.
This concept is closely related to blockchain technology. In developing the ecosystem and creating new products, blockchain exhibits spontaneous and somewhat random characteristics through its incentive-based systems (while maintaining a broad direction) - this is evident in the evolution of standards like Ordinals, BRC-20, and ERC-404. Although incentives can have a dual nature, blockchain has demonstrated that a digital world can be created where all entities move towards a common goal based on incentives, which is a significant achievement.
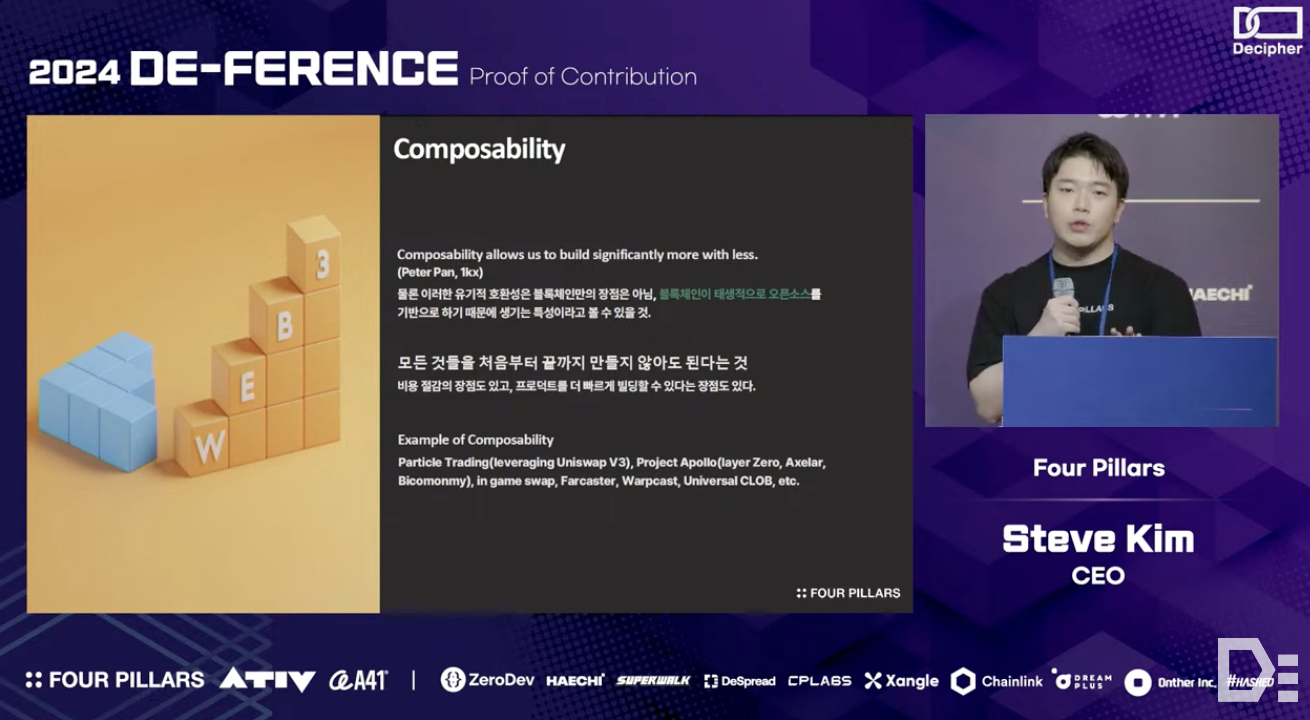
The second pillar highlighted by blockchain technology is 'composability'. As Peter Pan stated, “Composability allows us to build significantly more with less.”
Composability is crucial for blockchain and all open-source ecosystems, enabling developers to efficiently create new products by leveraging existing components rather than starting from scratch. This optimizes resources and allows teams to focus on core values, fostering rapid innovation.
Examples of this approach can be seen in projects like Particle Trading (Uniswap V3), Project Apollo (LayerZero, Axelar, Biconomy), Farcaster’s Frame, and Universal CLOB (Serum, Sei), which create new value by improving or reusing existing resources. Additionally, metaverse/gaming services like the widely discussed MapleStory, which require extensive resources, can benefit from existing infrastructures, allowing them to invest more in key values. Although blockchain has been criticized for its inefficiency in usability, its composability can make product building more efficient, akin to Standing on the Shoulders of Giants.
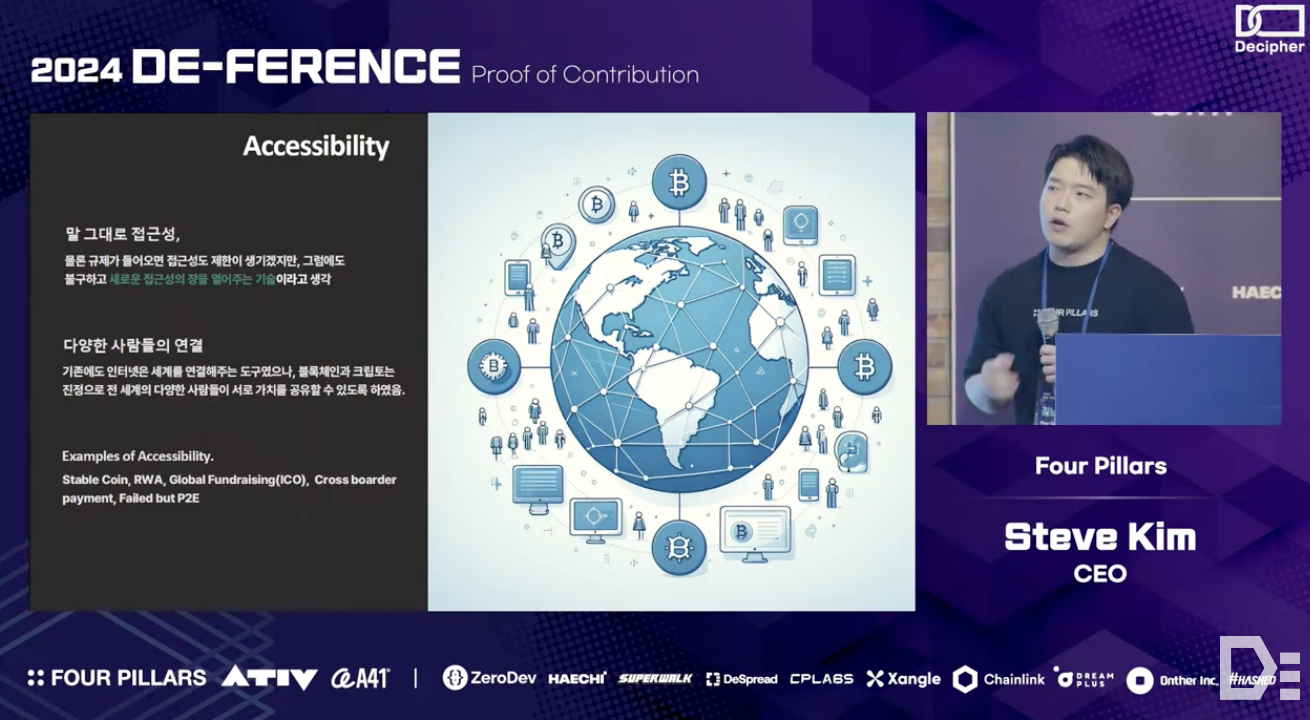
Blockchain technology is popular in specific communities because it transcends physical limitations, delivering value to various individuals and groups. For example, protocols like Ondo Finance offer people worldwide access to US short- and long-term government bonds or ETFs. This accessibility allows people to protect their assets by accessing new investments rather than being tied to their national currencies.
Blockchain's accessibility can also align incentives globally. Traditional social media platforms connect users worldwide but often fail to genuinely share values across different cultures. In contrast, crypto communities can share common values and align incentives, enabling a truly global internet experience.

Also, blockchain technology holds significant societal value. Its immutability, in particular, is closely linked to data reliability, enabling features like censorship resistance - these characteristics ensure data traceability, which in turn can create social and economic value.
While immutability may be less directly related to driving product innovation, it provides a unique value intrinsic to blockchain. For instance, examples such as Fox Group's content verification platform, critical content about Xi Jinping posted on the Ethereum network, and anti-China magazines published on Arweave are all possible due to blockchain's censorship resistance. In essence, blockchain's immutability plays an important role in socio-economic contexts and can enhance digital freedom of expression.

Considering all four values above, the essence of the blockchain industry lies in 'unintended spontaneity'. Even Ethereum’s founder, Vitalik Buterin, admitted he couldn't predict Ethereum's future. In the blockchain ecosystem, the system often evolves in ways not intended by its creators, as observed with numerous L1 and L2 projects.
Blockchain is a system that evolves organically through the onboarding of numerous participants and the resulting randomness, leading to unintended outcomes. Based on this 'collective complexity', blockchain creates new value through many trials and errors. This 'unintended spontaneity' is a crucial characteristic of the industry, and understanding it is essential for maintaining ongoing interest and engagement in the field. It also suggests that meaningful experimentation often involves collaborative efforts and diverse attempts rather than striving for individual success.

Despite its unique values and characteristics, the blockchain industry still has a long way to go, primarily due to the lack of sufficient Product-Market Fit (PMF). Verified PMF activities include creating chains, generating transaction fee revenue, receiving tokens as validators, investing, and etc. As people continue to participate in the blockchain ecosystem to strengthen existing PMFs or find new ones, it's essential to deeply consider the fundamental values that blockchain can offer. Four Pillars will continue to explore how it can contribute to this market through research and grow as a result.
Q: Decentralization has long been a key keyword for blockchain. However, looking at your presentation and recent industry trends, this keyword doesn't seem to stand out. What are your thoughts on this?
A: Decentralization was once a highly valued principle for me as well. But now, I see decentralization merely as a tool to achieve the four values I mentioned earlier. Instead of viewing blockchain as important because of decentralization, I believe that because blockchain is inherently decentralized, it can embody these four values. The reason why the keyword decentralization isn't mentioned as often recently is, I think, because the industry has grown weary. In reality, technology is meaningless if it isn't used. Thus, the crucial question for us should be, "How can we or why do we use blockchain?" rather than "Which chain is more decentralized?" Many protocols claim they are 'sufficiently decentralized.' We have reached a point where we need to focus on practical usability while accepting a certain degree of decentralization.
Q: You've described blockchain has a collective complexity, yet most blockchain projects expect consistent loyalty and behavior from their communities. How can blockchain projects be sustained in this paradoxical situation?
A: Complexity is not exclusive to blockchain; it exists across markets and encompasses all phenomena that often diverge from their intended course. The type of complexity I referred to in my presentation involves the unintentional creation of new things through the interactions of diverse individuals under a broad, overarching direction. The past decade of blockchain history, which has continually produced new innovations, exemplifies this type of complexity. Traditional systems operate as designed, limiting innovation, while blockchain functions on incentives, enabling various innovations and creative experiments. In short, we need to align on a broad direction but design a 'complex and random’ environment where new things can emerge under this direction through well-structured incentive systems. This way, projects can sustain and evolve continuously.
Overview
Sang Kim from the Open Source Warriors team presented various ways to contribute to the industry and shared their experiences of researching ERC-6900 and Uniswap V4 LVR Minimization Hook over the past semester, as well as contributing open-source code.
Comments
Open source has played a significant role in the continuous experimentation and emergence of new services in the blockchain ecosystem - it allows individuals to grow through publicly available code and helps them complement each other's weaknesses. The Open Source Warriors' presentation vividly shared this process, motivating many to participate more actively in the open-source ecosystem and demonstrating that contributing to open-source is not overly complex.
Below is a summary of Sang Kim's presentation.

The Open Source Warriors team was formed as a result of seeking other ways to contribute to the industry amidst the increasing research activities. They chose to contribute to open source, believing that their contributions could 1) enhance Decipher's global recognition, 2) make practical contributions to the ecosystem, and 3) be actively led by non-stakeholder entities like academic associations.
The common method of contributing to open source is through direct project involvement via code development. For example, websites like useweb3.xyz provide lists of projects, and developers can participate by sending pull requests to each project's GitHub repository. Besides code development, contributions can also be made by posting ideas or sharing research pieces on platforms like Ethereum Magician or Ethereum Research.
The Open Source Warriors team contributed by researching, implementing, and simulating the ERC-6900 standard's plugins and management, as well as the Uniswap V4 LVR-minimization Hook, using the aforementioned methods.
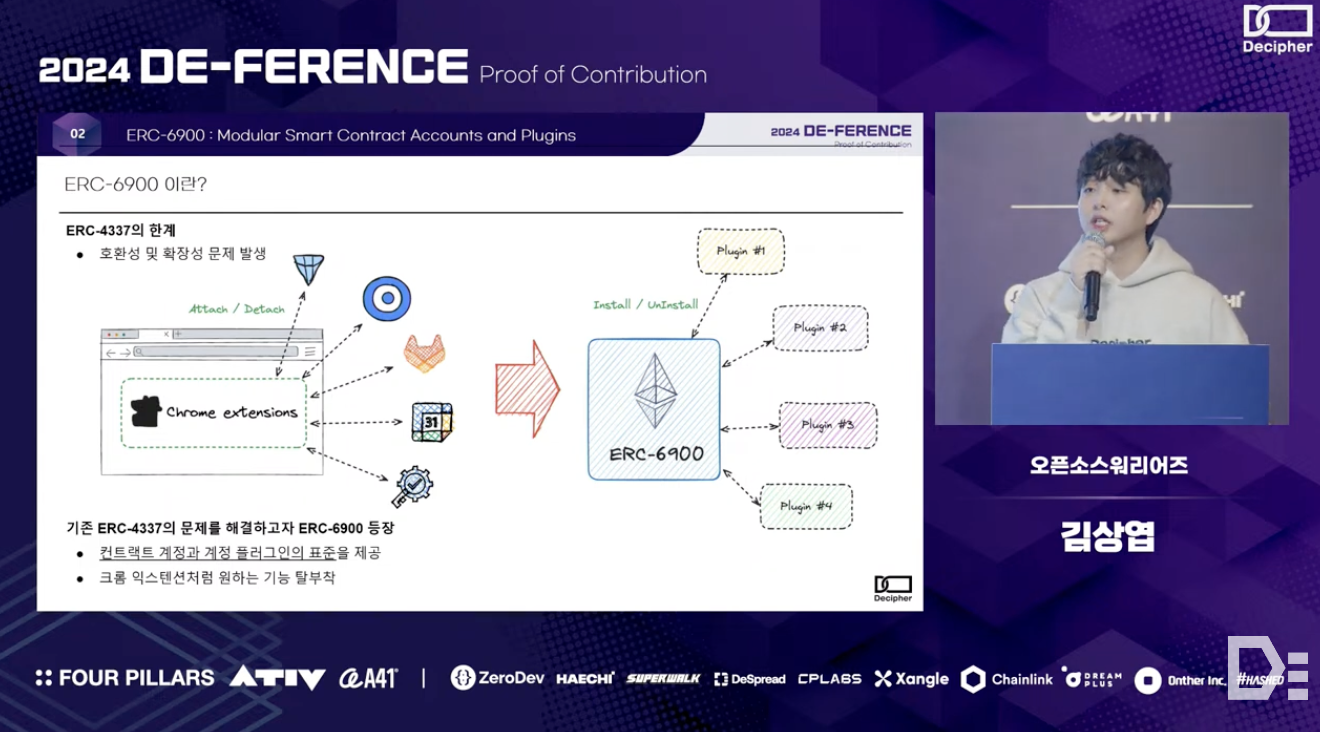
Currently, the widely used Account Abstraction (AA) on Ethereum is based on the ERC-4337 standard. The core idea of this standard is to implement logic at the application level, allowing individual smart accounts to possess the functionalities of both externally owned accounts (EOA) and contract accounts (CA). However, ERC-4337-based AA has limitations, such as a lack of standardization for smart accounts leading to compatibility issues and difficulties in modifying the functions that individual accounts can implement, resulting in scalability problems.
To address these limitations, ERC-6900 was introduced to establish standards for smart accounts and account plugins. ERC-6900 is modular, allowing easy addition or removal of individual modules, and features a proxy structure that simplifies function modifications. Additionally, from an application standpoint, it reduces implementation complexity by enabling interaction with smart accounts that use a unified standard rather than various configurations.
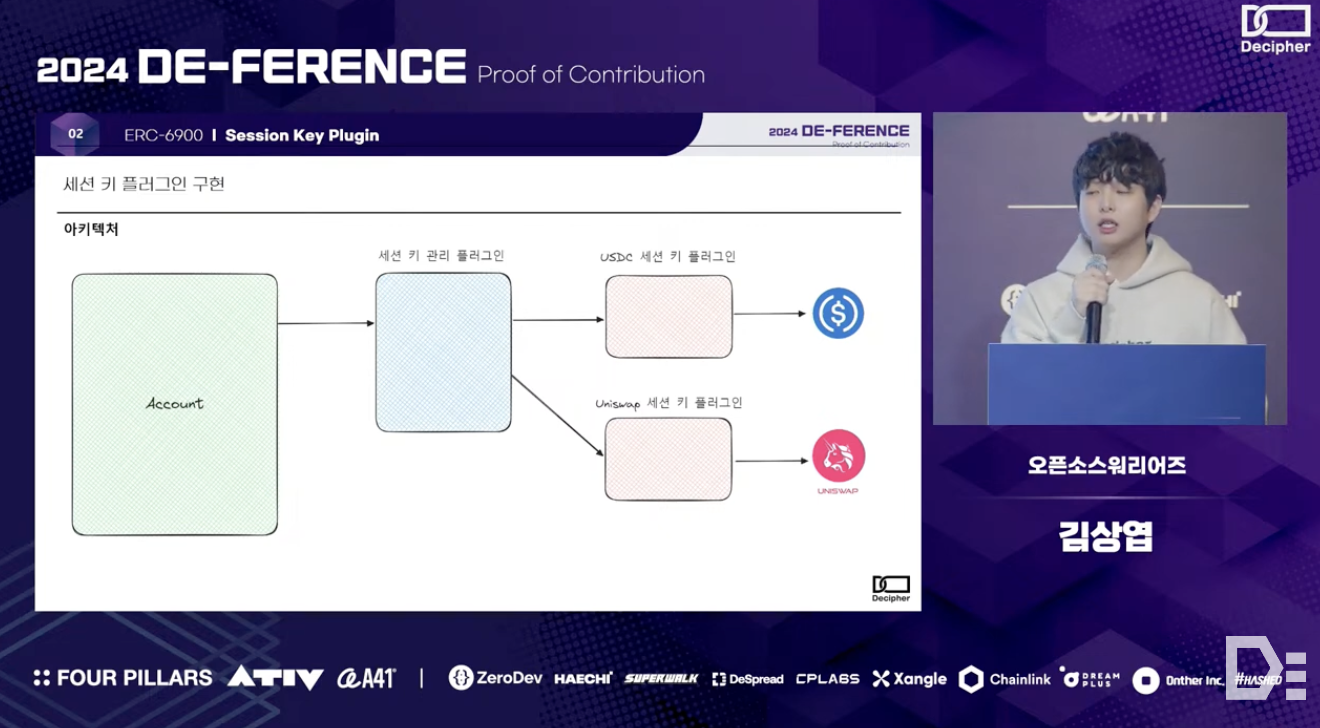
The Open Source Warriors team made two significant contributions to ERC-6900. The first is the development of a session key plugin. Session keys, a key feature of AA, allow partial account permissions to be delegated to external parties for a set duration. This feature can significantly enhance user experience, particularly in on-chain games and DeFi applications. Given the importance of security for session keys, the Open Source Warriors team ensured that session keys only operate on predetermined contracts and developed a hierarchical plugin management system to efficiently manage multiple session key plugins - more details can be found on GitHub.
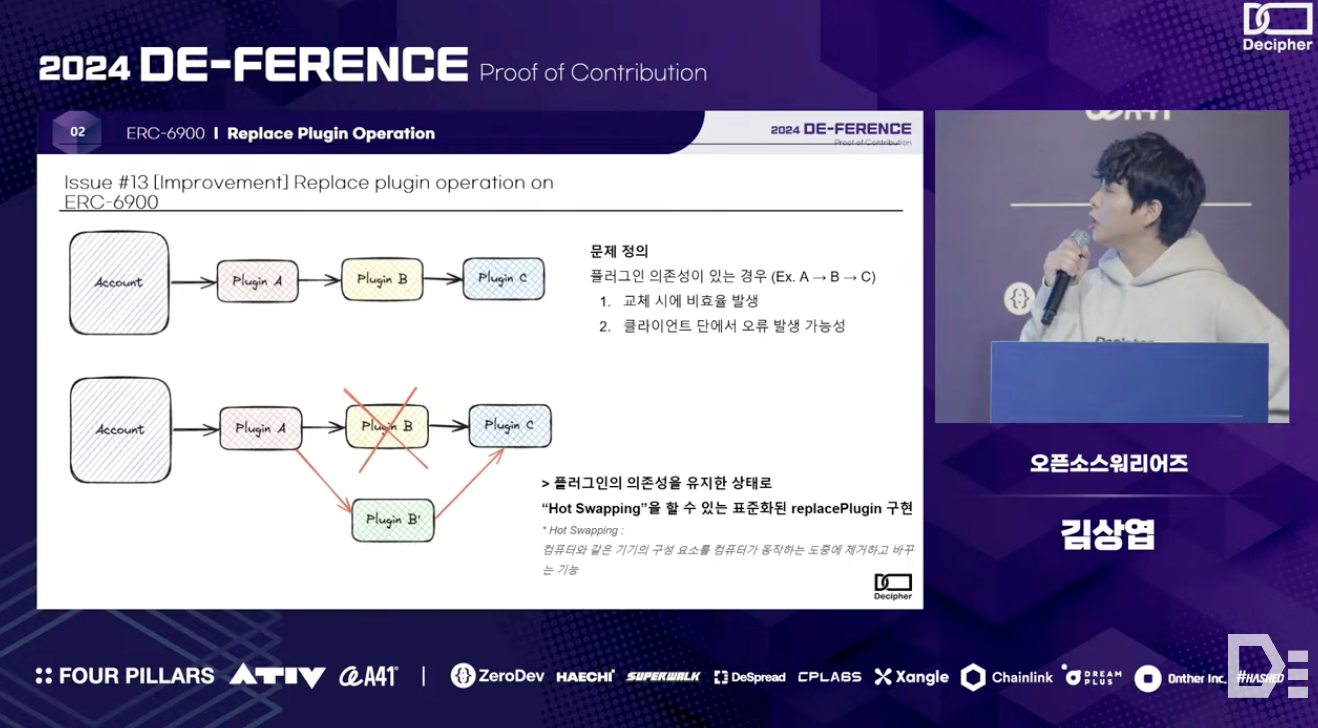
The second contribution from the Open Source Warriors team addresses dependency issues among ERC-6900 standard plugins through the implementation of replacePlugin, which utilizes hot swapping. This allows users to replace new plugins without the hassle of reinstalling all dependent plugins. They also improved plugin management by adopting a versioning system, enabling plugin replacement only in patch versions, and ensuring that only vetted plugins approved by a Committee are registered through a Version Registry. Additionally, since ERC-6900's diamond proxy structure stores data within plugins, data migration is required when plugins are replaced. The team implemented a separate function to safely delete data from the old plugin and transfer it to the new one.
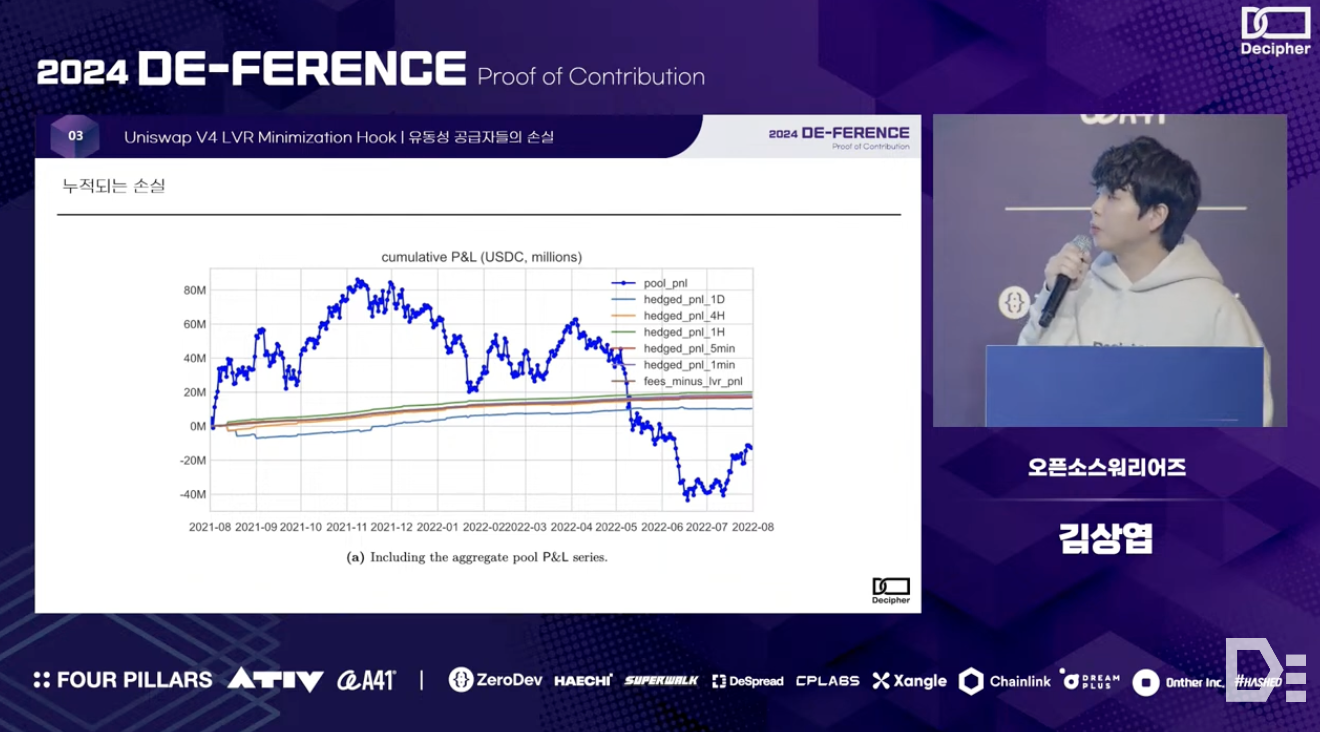
As seen in the example of the ETH-USDC pool in Uniswap V2 above, the cumulative PNL of the pool turns negative after a certain period following the initial liquidity provision. It is well known that this loss is primarily attributed to impermanent loss. However, it has recently been discovered that there are also losses due to LVR (Loss-versus-Rebalancing) - LVR loss refers to the (potential) loss incurred by liquidity providers due to arbitrage opportunities arising from delayed price reflection in the liquidity pool (e.g., decentralized liquidity pools with relatively low liquidity typically reflect prices more slowly than centralized exchanges).
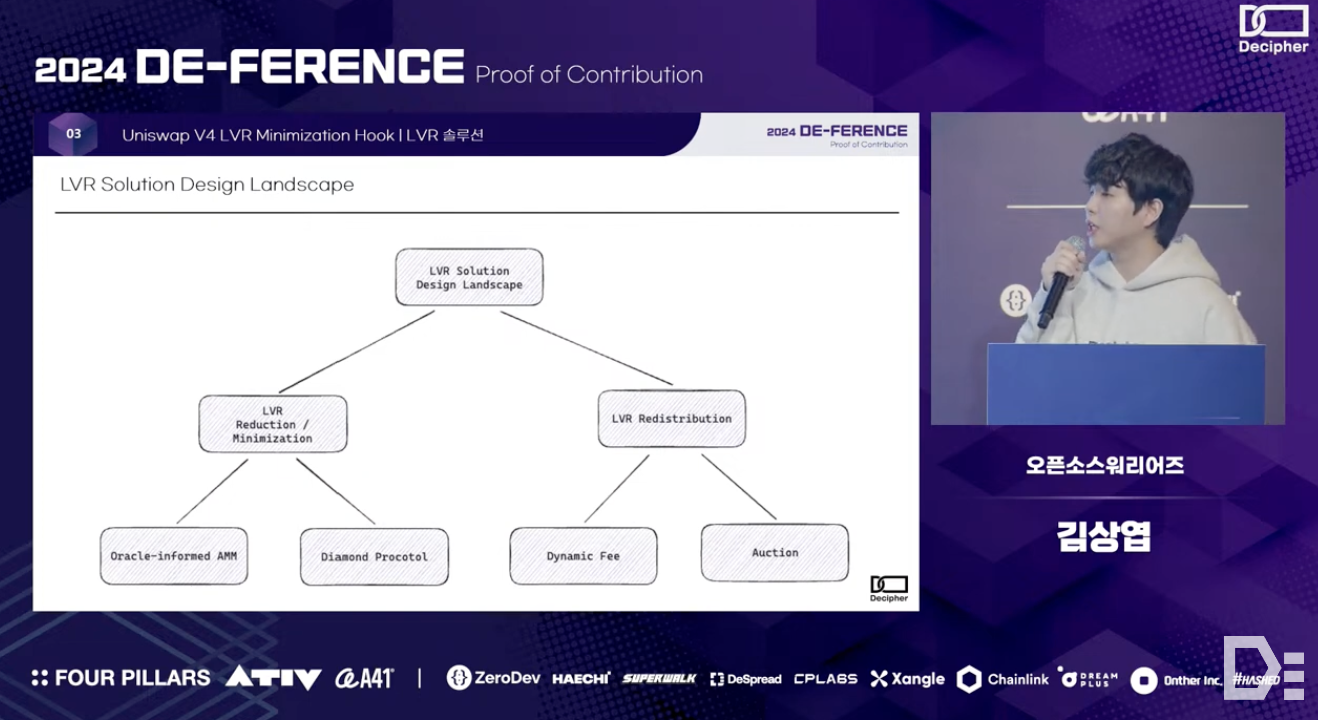
There are two approaches to addressing LVR, as shown in above image: minimizing LVR or redistributing LVR. The Open Source Warriors team has researched the Diamond Protocol method and Dynamic Fee application.
The Diamond Protocol method reduces costs for liquidity providers and increases their returns by sharing a portion of the arbitrage profits with the liquidity pool - in this protocol, arbitrageurs who provide sufficient collateral share part of their profits from arbitrage with the liquidity pool. This process allows the liquidity pool to adjust token prices to the market price and store excess tokens in a vault, which are then dynamically managed and moved back to the pool as needed, thereby minimizing the pool's losses.
The impact of LVR varies depending on how strategies are implemented in each specific process - in the process of redistributing tokens from the vault to the pool, the 'Conversion vs. Futures Strategy' involves arbitrageurs exchanging tokens in the Diamond Protocol's vault with the pool. They then create futures contracts corresponding to the changed balance and manage these through periodic auctions. This approach aligns the pool's price with the market price and minimizes LVR. Additionally, the proportion of profits(i.e., beta) that arbitrageurs share with the liquidity pool can affect LVR loss. The 'Dynamic Fee Strategy' dynamically adjusts the beta proportion according to token price volatility to minimize LVR loss.
Detailed implementation and simulation results of these methods can be found at the following link, where the Open Source Warriors team has proposed optimal conditions for minimizing LVR loss through their simulations.
Q: You've created a key management system to efficiently manage multiple session keys. What measures are in place to prevent this system itself from being hacked?
A: Rather than assuming the session key contract will be hacked, we designed the architecture to prevent the entities assigned session keys from acting maliciously. Thus, the security aspect I emphasized in the presentation is more about behavioral control. We have significantly restricted the actions that session keys can perform and ensured that each session key has a designated valid period. Preventing contract hacking itself should be managed through thorough audits and reviews.
Q: It was helpful to hear your guidance and experiences on how researchers and developers can contribute to the Ethereum or blockchain ecosystem. Were there any particularly challenging episodes during this process?
A: Before joining the Open Source Warriors team, my personal contributions to ERC-4337 were challenging due to slow communication and difficulty in meeting deadlines, as we were not formally contracted to collaborate. However, in this project, Alchemy, our collaboration partner, has been excellent in communication, making the process much smoother.
Overview
The Drifter on the Bit team focused on the fundamental purpose of Bitcoin as a currency and covered the overview of the Lightning Network to develop a remittance service that many people can use. They explored potential business opportunities through this network and created & demonstrated a prototype.
Comments
As Steve mentioned in his presentation, we have not yet observed clear use cases from existing smart contract platforms compared to our imagined future. Conversely, it may be more realistic to first confirm clear use cases in the most basic function of a blockchain network—remittance (i.e., value transfer). The significance of the Drifter on the Bit team lies in their focus on discussing the essential and practical functions of the Lightning Network that can be implemented immediately, rather than concentrating on the rapidly evolving and experimental trends of the industry.
Recently, Bitcoin has gained significant attention as its value as an asset has been recognized, particularly with the approval of ETFs. However, Bitcoin was originally created to function as a P2P network currency for exchanging digitized value, but inefficiencies for small remittances and long transaction times make it difficult to function effectively as a currency.
To address these issues, the Lightning Network was developed to handle small remittances and payments off-chain quickly, without recording every transaction on-chain. The Lightning Network allows individual nodes to lock funds in a logical channel and perform off-chain transactions with low fees within the limits of those funds. The final balances of each participant are then processed by aggregating multiple off-chain transactions and recording only the final state on-chain.
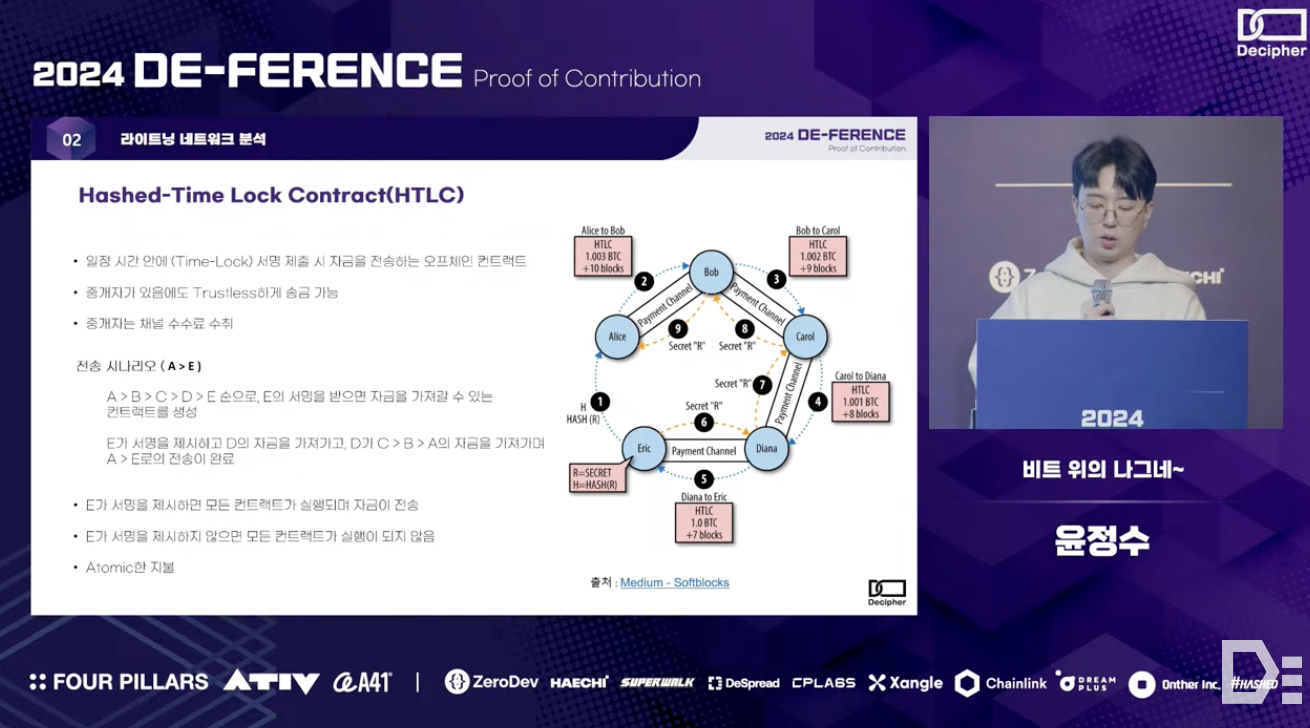
However, opening channels between all nodes in the Lightning Network to ensure transaction autonomy is highly inefficient. Thus, the Lightning Network service uses a channel graph based on HTLC (Hashed-Time Lock Contract) to enable trustless communication between nodes that are not directly connected - intermediary nodes facilitating these transactions use an incentive system (i.e., fee revenue) and Onion Encryption technology to process the intended transactions through other interconnected intermediary nodes. The process of directly connecting two nodes by opening a channel involves: 1) locking funds with a Funding Tx, 2) recording the state of funds in the node's database after off-chain transactions with a Commitment Tx, and 3) settling the funds with a Settlement Tx.
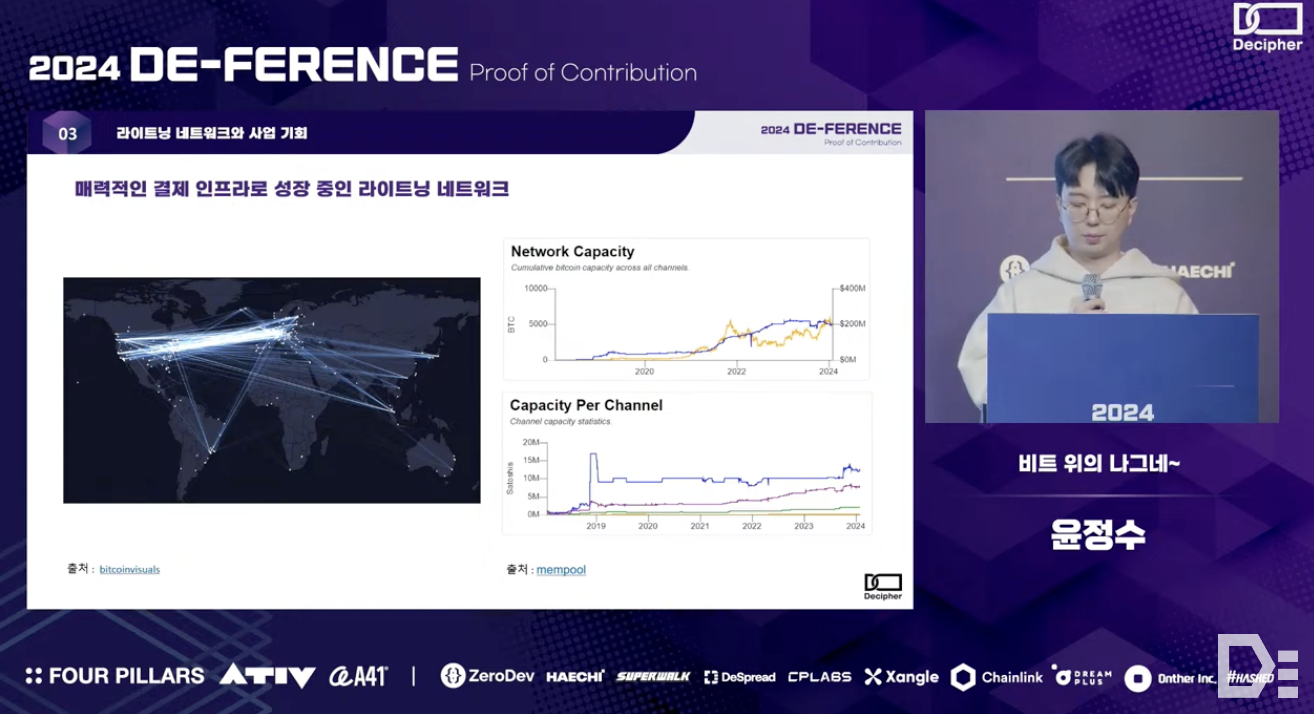
Adoption rates for remittance services* utilizing the Lightning Network have steadily increased, with the network capacity exceeding $200 million as of January 30th this year. This expansion presents various business opportunities - firstly, the Lightning Network, which boasts an average fee of 0.07%, has the potential to replace the high fees (i.e., 2-3%) in the current mobile POS market. Secondly, it can enter the hot wallet market, like MetaMask or Phantom, to secure a portion of the swap fees.
However, for various Lightning Network wallet services (e.g., Wallet of Satoshi, Strike, Alby, River, etc.) to deploy these business initiatives in Korea, several aspects need consideration. From an accounting perspective, 1) ambiguous virtual asset accounting standards and 2) the potential for tax evasion using Bitcoin payments must be considered. Legally, aspects like 1) virtual asset service provider(VASP) registration including KYC / AML, 2) electronic payment processing business registration, and 3) potential applicability of the Foreign Exchange Transactions Act should be addressed.
*The described remittance process assumes both the sender and receiver operate Lightning nodes. Therefore, most widely used remittance services provide custodial Lightning Network wallets for users.
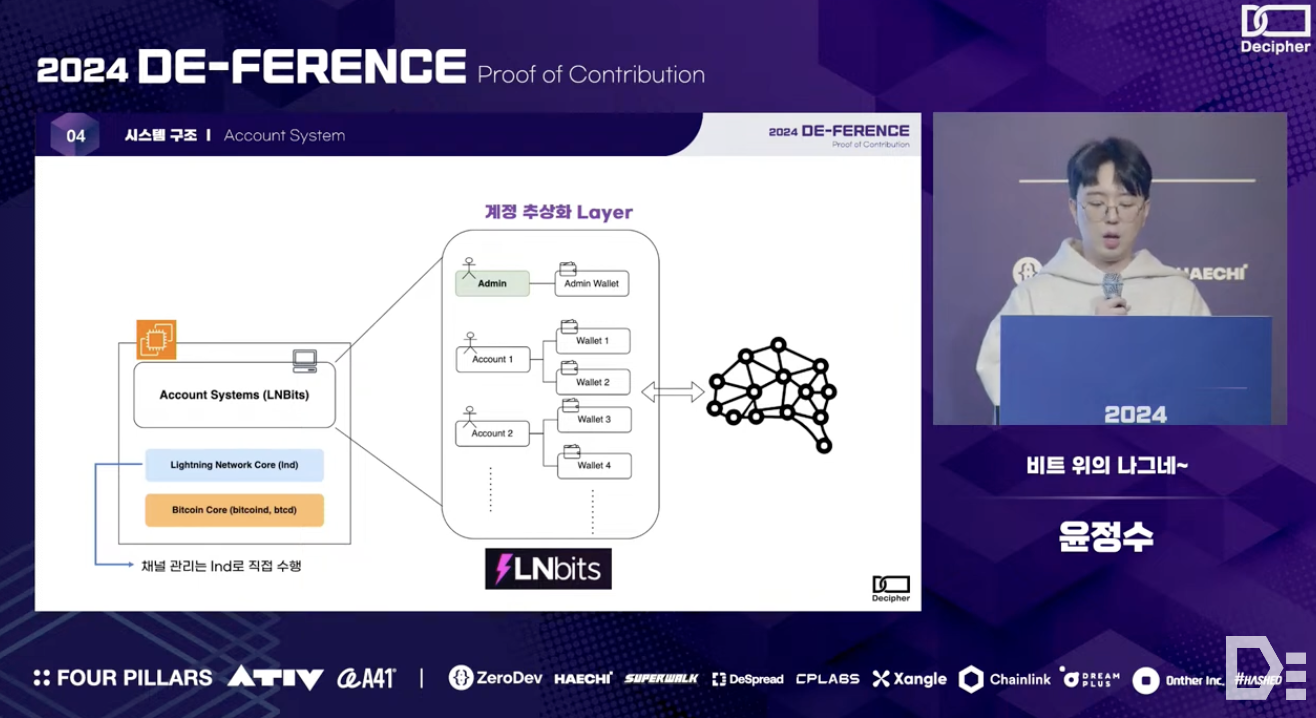
Considering the structure of the Lightning Network and the aforementioned considerations, a prototype for a custodial Lightning wallet service could be designed as follows.
The service architecture consists of 1) a Bitcoin node (i.e., btcd) that handles communication with the Bitcoin mainnet, 2) an LND process that communicates with the Lightning Network, and 3) an Account System* layer that abstracts accounts for users to manage their Lightning Network wallets custodially - while the LND process manages communication with the Lightning Network, such as channel creation and management, the Account System handles invoice management and account balances.
*In this prototype demonstration, the Account System was implemented using the open-source LNbits.
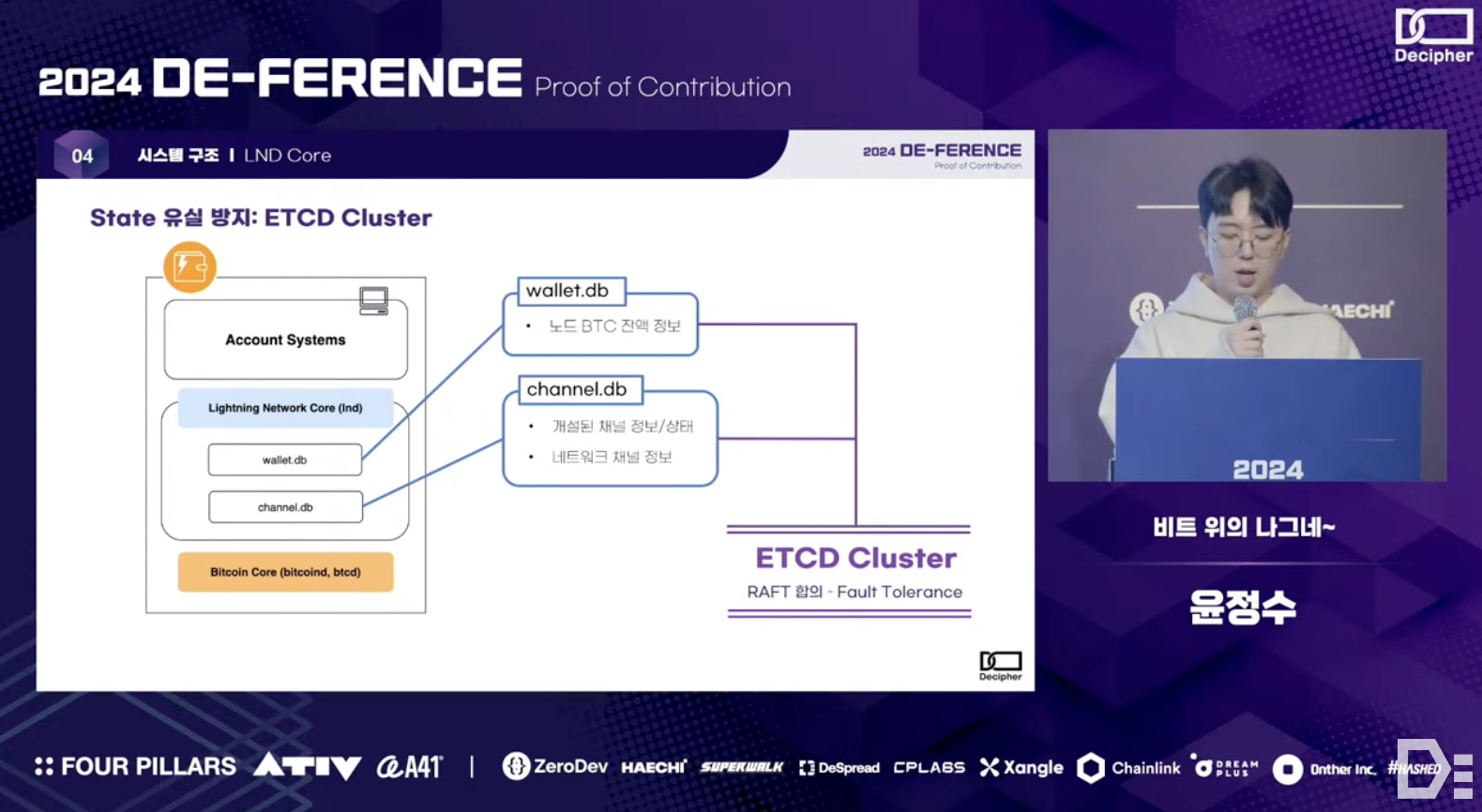
In this structure, it's crucial not to manage the backend DB as a single point of failure to prevent loss of BTC balance information stored in wallet.db and channel information stored in channel.db in case of node failures.
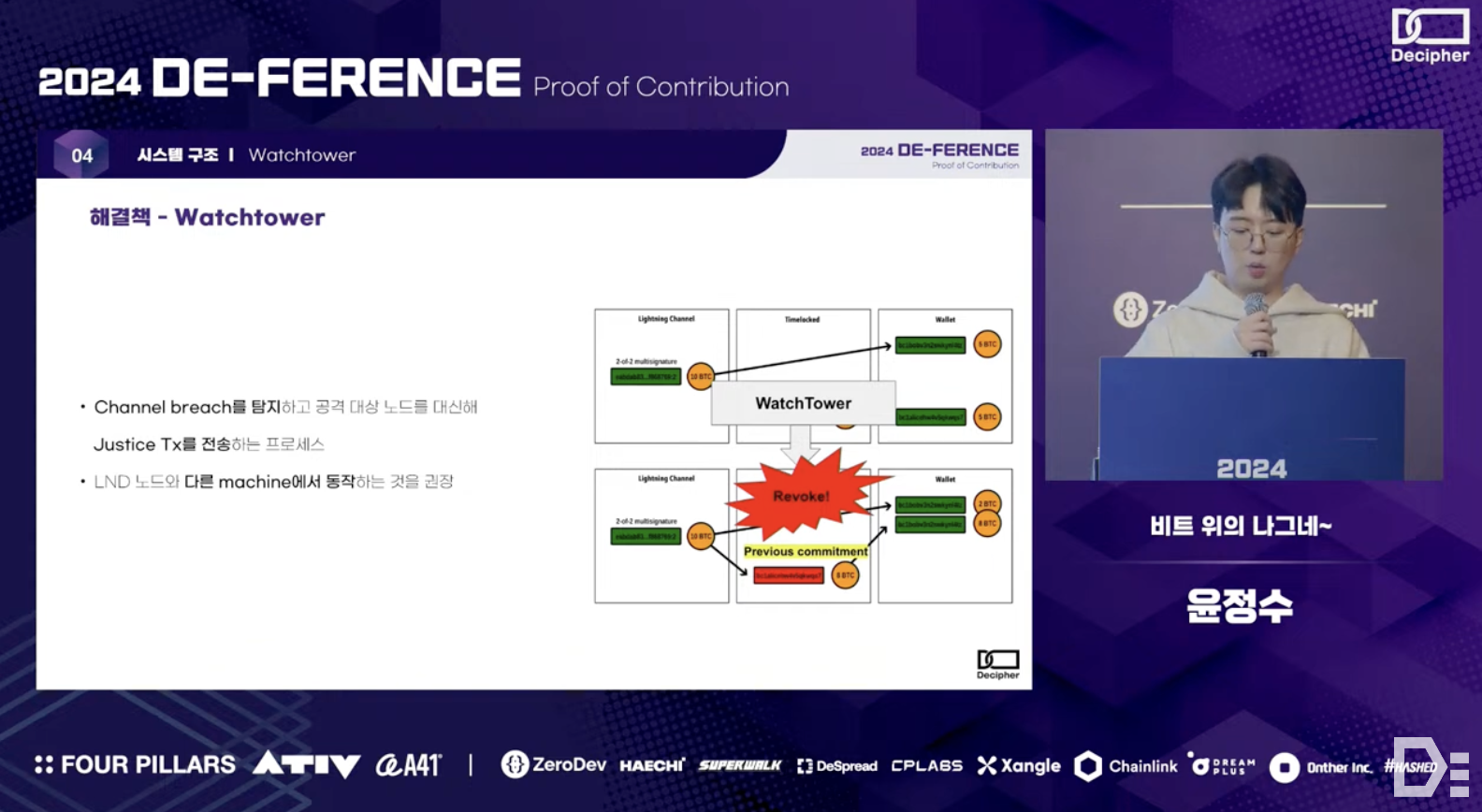
Another key element to enhance node security is preparedness against Channel Breach Attacks. This type of attack occurs when an attacker submits a previous Commitment Tx favorable to them during an off-chain transaction to take more funds. To prevent this, the counterparty node must be able to issue a Justice Tx within the Timelock period to confiscate the malicious node's funds. If this process fails, it can result in a loss of funds.
To prevent such scenarios in the first place, the Drifter on the Bit team implemented a Watchtower process - the Watchtower monitors the status of Commitment Txs on the Lightning Network and the main network to detect Channel Breach Attacks and sends a Justice Tx on behalf of the attacked node. This process should be also designed to operate on multiple LND nodes, not just the leader LND node, considering potential node failures.
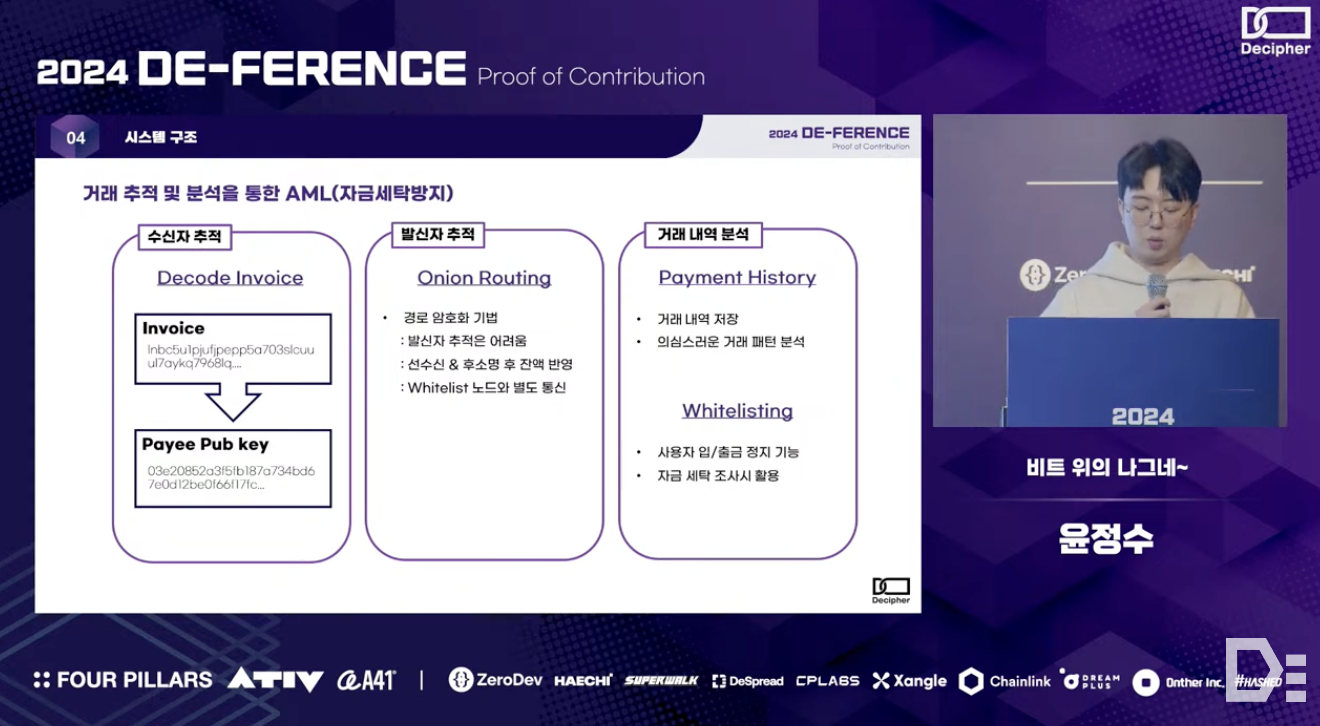
Beyond the system structure, addressing legal considerations (i.e., KYC, AML) requires solutions in three areas: recipient tracking, sender tracking, and transaction history analysis.
For recipient tracking, parsing a Lightning invoice defined by the BOLT #11 (Basis of Lightning Technology) specification allows finding the public key of the recipient node. Similar to the practice of many exchanges, remittances above a certain amount could be restricted to whitelisted node public keys.
Sender tracking is relatively challenging due to Onion Encryption, where it facilitates Hop Payments in the Lightning Network but makes tracking the sender difficult at the same time. Thus, for investigating the source of funds, a ‘receive first & verify later’ approach, where the balance is received first and then verified, can be employed.
Lastly, to comply with AML requirements for potential future investigations, transaction history should be stored in the payment history of the Account System.
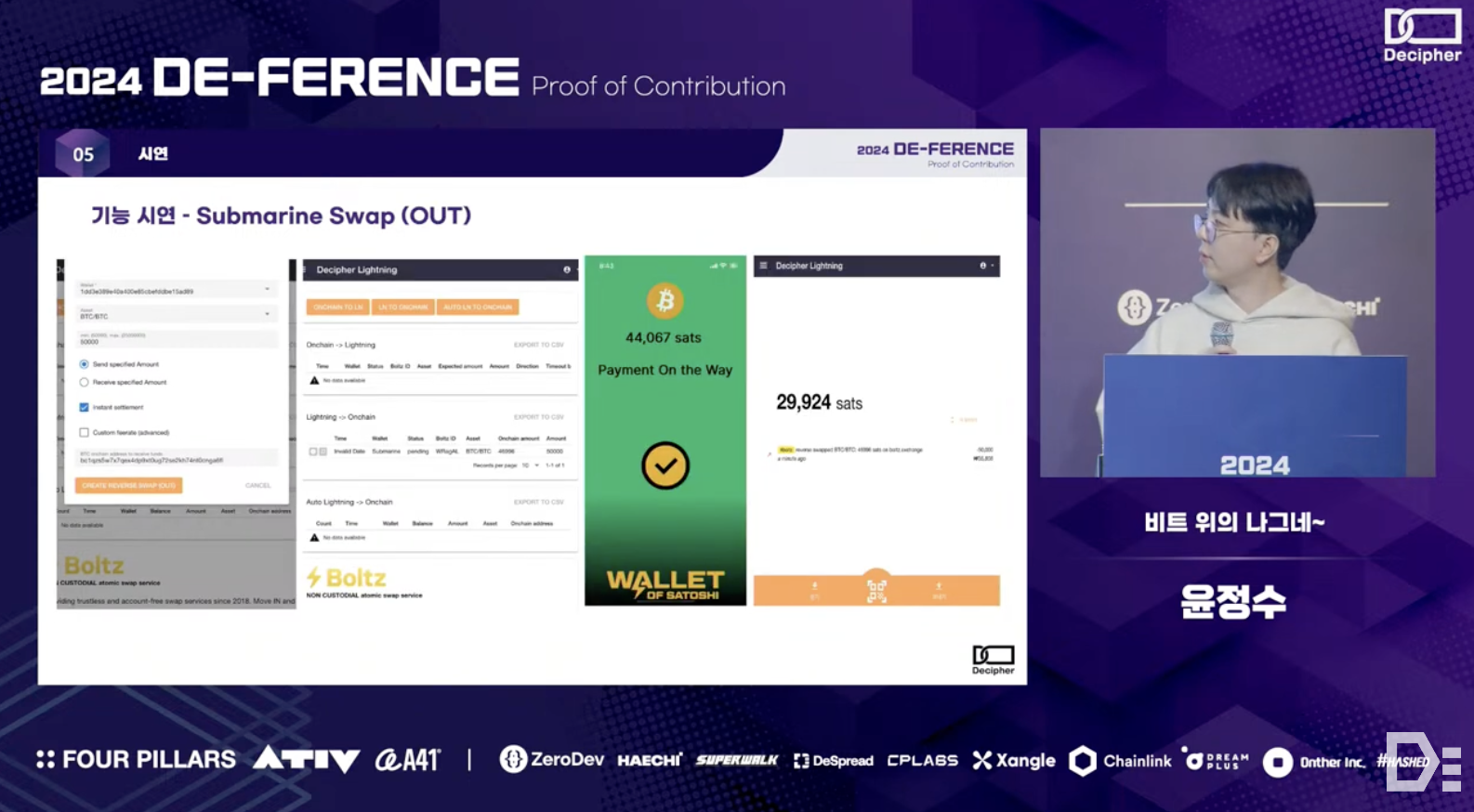
The prototype created according to the content in 3.3 demonstrated account registration, KYC, invoice creation and payment, and Submarine Swap (i.e., transferring the balance from the Lightning Network to on-chain) in the conference, but the link is now expired.
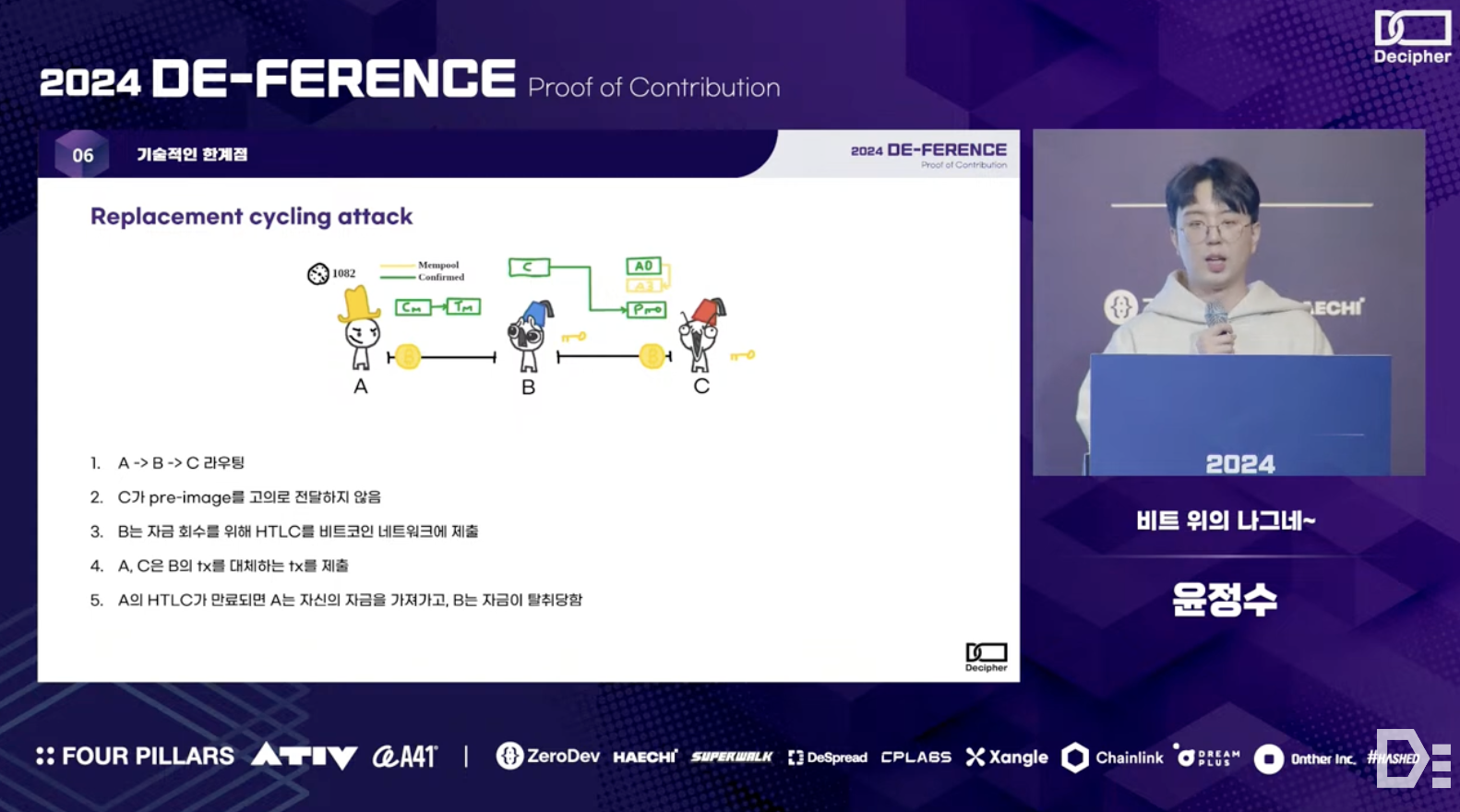
Including the demonstrated prototype, off-chain payment services are inherently more vulnerable to security issues compared to on-chain payments. For example, there can be a malicious attack known as a Replacement Cycling Attack*. In this attack, attackers A and C collude to steal B's funds - when B intermediates a payment from A to C, C intentionally does not deliver the pre-image. When B broadcasts a transaction to recover the funds, A and C broadcast anopther transaction with a higher fee, removing B's transaction from the mempool. As a result, B's funds can be stolen.
*Addressing such vulnerability requires core-level modifications to the protocol.
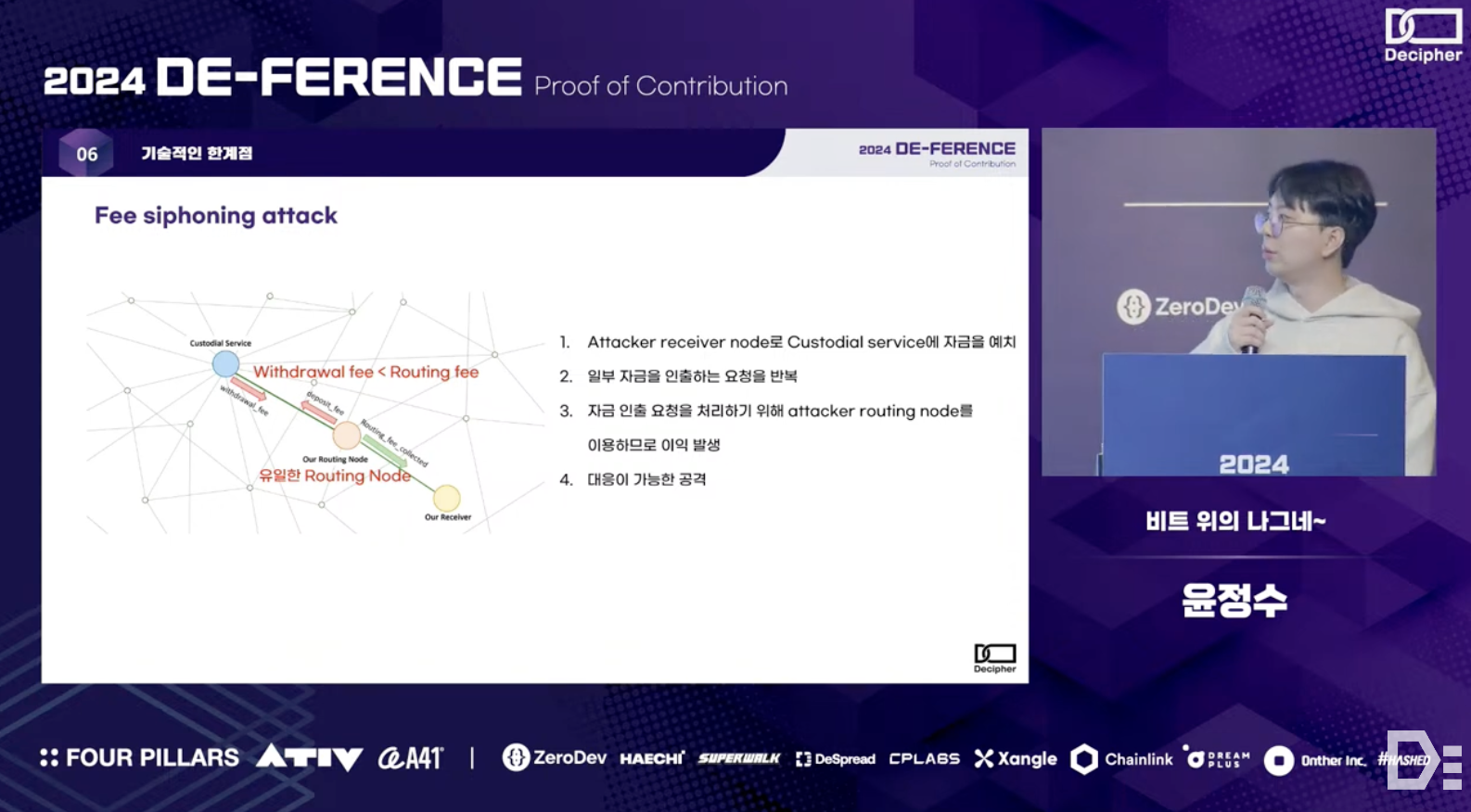
Alternatively, a Fee Siphoning Attack could occur - this attack happens when the routing fee is higher than the withdrawal fee, leading malicious actors to repeatedly extract routing fees by forcing a custodial wallet to use a specific routing path. However, this can be prevented with appropriate fee settings.
The Drifter on the Bit team summarized several insights and implications after building and using the prototype of Lightning Network service - firstly, they highlighted the significant potential of applying the existing seamless remittance experience (e.g., Venmo, Toss) to international remittance, despite the prototype service having limited channel liquidity and a small number of channels. Additionally, the team found that using an open network(i.e., LNbits) significantly reduced the costs of building the account system. However conversely, they also realized that leveraging such open network necessitates enhancing various security initiatives to ensure the actual operation of the service. Furthermore, since the study aimed to implement a service usable by many people, it suggests that exchanges and brokerage firms could adopt this idea to enhance their own services. However, they emphasized the importance of complying with KYC and AML regulations to prevent potential abuse due to the anonymity in service operation.
There were no questions regarding this presentation.
※ This article series covers the DeFerence 2024 event, sponsored by Four Pillars. This article is the first part of the series, and the next part will be published soon - the theme of the next part is ‘Blockchain, Reaching the Masses.’
Dive into 'Narratives' that will be important in the next year